Lately I’ve done a lot of lab testing with access switches and security features. To be more precise, I’ve done 802.1X testing on Cisco switches with the new IBNS 2.0 configuration style – but that’s another story.
During testing, bogus MAC addresses are sent in frames from the ESXi host to my switch, which interferes with some security features …
So here’s a sample lab exhibit:
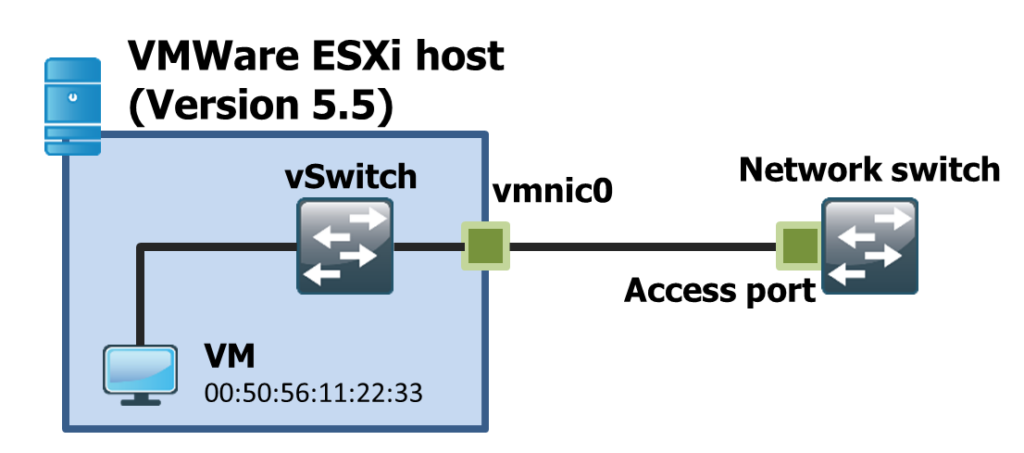
We have an access switch connected to an ESXi host with one active virtual machine. No 802.1Q VLAN tagging is in place. The goal is to test a single client connected to on a physical switch port. The client has the MAC 00:50:56:11:22:33.
The switch port is configured as 802.1X authenticator in multi domain mode. So one MAC address in the configured data VLAN (switchport access vlan …) and one MAC address in the voice VLAN (switchport voice vlan …) is allowed.
During testing, the switch port on the network switch raises a security violation and the switch port goes into error disable state (security-violation), because a new MAC address is seen on the switch port. The MAC addresses are in the range 00:00:00:00:00:01 – 00:00:00:00:00:04. This behavior is reproducable in case the network adapter in the VM guest operating system (Windows) is disabled and enabled again.
This is very, very disruptive and annoying during testing. First of all I captured on the VM itself if these frames are generated by my guest operating system – fail – no success at all! So, after I had physical access to the lab, I configured a SPAN session on that access port and voila, I captured the bad frames, which are reverse ARP frames.
These RARP frames doesn’t make any sense, because they contain only the bogus MACs mentioned above. After some <insert-your-search-engine-here>’ing for VMWare and RARP I stumbled upon this KB article:
https://kb.vmware.com/selfservice/microsites/search.do?language=en_US&cmd=displayKC&externalId=1556
The feature “Notify Switches” has something to do with the RARP behavior in ESXi. And this feature makes perfectly sense in a VMotion migration scenario or in case the ESXi host is connected redundantly. In case the VM moves to a new link the vSwitch updates the physical switch MAC address table using RARP.
However, I have no idea why this bogus MAC in the RARP frames is generated and furthermore I don’t get the good idea behind this (except the fact that this provides the content for my first blog post of course).
Long story short: If you’re in a lab testing environment along with security features as 802.1X, MAB or port-security and simulate you clients using VMWare, make sure to disable the “Notify Switches” setting in your vSwitch or port-group configuration in VMware. Please refer to my linked VMWare KB article to find that setting.
However, if you are in a productive environment, the setting makes perfectly sense and should be enabled in case of link redundancy (no port-channels) or vMotion scenarios.


0 Comments