So one generic method to capture wireless frames is using Linux. There are multiple distributions, which are specialized on this (an example is Kali Linux).
However, standard Linux distributions may be used as well. This how to is created considering Ubuntu 16.04 LTS on a laptop with an integrated “Intel(R) Dual Band Wireless-AC 7260” adapter.
Unnecessary to mention, that your wireless connection is not availabe during capture. Also I’m not responsible if you break your Linux system!
Of course there are some helping tools like “airmon-ng” or “airodump”, which assists our traffic sniffing goal, but I try to focus on the built-in Linux fuctionality.
Preparations
First of all we should check if our wireless adapter supports the monitoring mode. If the adapter does not support this, only frames from and to the WLAN station can be captures along with broad- and Multicast frames.
So what’s the name of our wireless adapter in Linux:
iw devWill give you the output (example):
phy#0
Unnamed/non-netdev interface
wdev 0x2
addr 80:86:f2:6d:58:ae
type P2P-device
Interface wlp2s0
ifindex 3
wdev 0x1
addr 80:86:f2:6d:58:ad
type managedSo for the “iw” tool the device is named “phy0“. The interface name is “wlp2so”
To check if the adapter supports monitor mode, issue the command:
iw phy0 infoWill give you the output (example) along with tons of other interesting stats about your adapter. But in line 20 (section “supported interface modes”) we can see that the “monitor” mode is supported.
Wiphy phy0
max # scan SSIDs: 20
max scan IEs length: 425 bytes
Retry short limit: 7
Retry long limit: 4
Coverage class: 0 (up to 0m)
Device supports RSN-IBSS.
Device supports AP-side u-APSD.
Supported Ciphers:
* WEP40 (00-0f-ac:1)
* WEP104 (00-0f-ac:5)
* TKIP (00-0f-ac:2)
* CCMP (00-0f-ac:4)
* CMAC (00-0f-ac:6)
Available Antennas: TX 0 RX 0
Supported interface modes:
* IBSS
* managed
* AP
* AP/VLAN
* monitor
* P2P-client
* P2P-GO
* P2P-device
Band 1:
Capabilities: 0x11e2
HT20/HT40
Static SM Power Save
RX HT20 SGI
RX HT40 SGI
TX STBC
RX STBC 1-stream
Max AMSDU length: 3839 bytes
DSSS/CCK HT40
Maximum RX AMPDU length 65535 bytes (exponent: 0x003)
Minimum RX AMPDU time spacing: 4 usec (0x05)
HT TX/RX MCS rate indexes supported: 0-15
Bitrates (non-HT):
* 1.0 Mbps
* 2.0 Mbps (short preamble supported)
* 5.5 Mbps (short preamble supported)
* 11.0 Mbps (short preamble supported)
* 6.0 Mbps
* 9.0 Mbps
* 12.0 Mbps
* 18.0 Mbps
* 24.0 Mbps
* 36.0 Mbps
* 48.0 Mbps
* 54.0 Mbps
Frequencies:
* 2412 MHz [1] (22.0 dBm)
* 2417 MHz [2] (22.0 dBm)
* 2422 MHz [3] (22.0 dBm)
* 2427 MHz [4] (22.0 dBm)
* 2432 MHz [5] (22.0 dBm)
* 2437 MHz [6] (22.0 dBm)
* 2442 MHz [7] (22.0 dBm)
* 2447 MHz [8] (22.0 dBm)
* 2452 MHz [9] (22.0 dBm)
* 2457 MHz [10] (22.0 dBm)
* 2462 MHz [11] (22.0 dBm)
* 2467 MHz [12] (22.0 dBm) (no IR)
* 2472 MHz [13] (22.0 dBm) (no IR)
Band 2:
Capabilities: 0x11e2
HT20/HT40
Static SM Power Save
RX HT20 SGI
RX HT40 SGI
TX STBC
RX STBC 1-stream
Max AMSDU length: 3839 bytes
DSSS/CCK HT40
Maximum RX AMPDU length 65535 bytes (exponent: 0x003)
Minimum RX AMPDU time spacing: 4 usec (0x05)
HT TX/RX MCS rate indexes supported: 0-15
VHT Capabilities (0x038071a0):
Max MPDU length: 3895
Supported Channel Width: neither 160 nor 80+80
short GI (80 MHz)
TX STBC
SU Beamformee
VHT RX MCS set:
1 streams: MCS 0-9
2 streams: MCS 0-9
3 streams: not supported
4 streams: not supported
5 streams: not supported
6 streams: not supported
7 streams: not supported
8 streams: not supported
VHT RX highest supported: 0 Mbps
VHT TX MCS set:
1 streams: MCS 0-9
2 streams: MCS 0-9
3 streams: not supported
4 streams: not supported
5 streams: not supported
6 streams: not supported
7 streams: not supported
8 streams: not supported
VHT TX highest supported: 0 Mbps
Bitrates (non-HT):
* 6.0 Mbps
* 9.0 Mbps
* 12.0 Mbps
* 18.0 Mbps
* 24.0 Mbps
* 36.0 Mbps
* 48.0 Mbps
* 54.0 Mbps
Frequencies:
* 5180 MHz [36] (22.0 dBm) (no IR)
* 5200 MHz [40] (22.0 dBm) (no IR)
* 5220 MHz [44] (22.0 dBm) (no IR)
* 5240 MHz [48] (22.0 dBm) (no IR)
* 5260 MHz [52] (22.0 dBm) (no IR, radar detection)
DFS state: usable (for 730 sec)
DFS CAC time: 60000 ms
* 5280 MHz [56] (22.0 dBm) (no IR, radar detection)
DFS state: usable (for 730 sec)
DFS CAC time: 60000 ms
* 5300 MHz [60] (22.0 dBm) (no IR, radar detection)
DFS state: usable (for 730 sec)
DFS CAC time: 60000 ms
* 5320 MHz [64] (22.0 dBm) (no IR, radar detection)
DFS state: usable (for 730 sec)
DFS CAC time: 60000 ms
* 5500 MHz [100] (22.0 dBm) (no IR, radar detection)
DFS state: usable (for 730 sec)
DFS CAC time: 60000 ms
* 5520 MHz [104] (22.0 dBm) (no IR, radar detection)
DFS state: usable (for 730 sec)
DFS CAC time: 60000 ms
* 5540 MHz [108] (22.0 dBm) (no IR, radar detection)
DFS state: usable (for 730 sec)
DFS CAC time: 60000 ms
* 5560 MHz [112] (22.0 dBm) (no IR, radar detection)
DFS state: usable (for 730 sec)
DFS CAC time: 60000 ms
* 5580 MHz [116] (22.0 dBm) (no IR, radar detection)
DFS state: usable (for 730 sec)
DFS CAC time: 60000 ms
* 5600 MHz [120] (22.0 dBm) (no IR, radar detection)
DFS state: usable (for 730 sec)
DFS CAC time: 60000 ms
* 5620 MHz [124] (22.0 dBm) (no IR, radar detection)
DFS state: usable (for 730 sec)
DFS CAC time: 60000 ms
* 5640 MHz [128] (22.0 dBm) (no IR, radar detection)
DFS state: usable (for 730 sec)
DFS CAC time: 60000 ms
* 5660 MHz [132] (22.0 dBm) (no IR, radar detection)
DFS state: usable (for 730 sec)
DFS CAC time: 60000 ms
* 5680 MHz [136] (22.0 dBm) (no IR, radar detection)
DFS state: usable (for 730 sec)
DFS CAC time: 60000 ms
* 5700 MHz [140] (22.0 dBm) (no IR, radar detection)
DFS state: usable (for 730 sec)
DFS CAC time: 60000 ms
* 5720 MHz [144] (22.0 dBm) (no IR, radar detection)
DFS state: usable (for 446 sec)
DFS CAC time: 0 ms
* 5745 MHz [149] (22.0 dBm) (no IR)
* 5765 MHz [153] (22.0 dBm) (no IR)
* 5785 MHz [157] (22.0 dBm) (no IR)
* 5805 MHz [161] (22.0 dBm) (no IR)
* 5825 MHz [165] (22.0 dBm) (no IR)
Supported commands:
* new_interface
* set_interface
* new_key
* start_ap
* new_station
* new_mpath
* set_mesh_config
* set_bss
* authenticate
* associate
* deauthenticate
* disassociate
* join_ibss
* join_mesh
* remain_on_channel
* set_tx_bitrate_mask
* frame
* frame_wait_cancel
* set_wiphy_netns
* set_channel
* set_wds_peer
* start_sched_scan
* probe_client
* set_noack_map
* register_beacons
* start_p2p_device
* set_mcast_rate
* channel_switch
* Unknown command (104)
* Unknown command (105)
* connect
* disconnect
Supported TX frame types:
* IBSS: 0x00 0x10 0x20 0x30 0x40 0x50 0x60 0x70 0x80 0x90 0xa0 0xb0 0xc0 0xd0 0xe0 0xf0
* managed: 0x00 0x10 0x20 0x30 0x40 0x50 0x60 0x70 0x80 0x90 0xa0 0xb0 0xc0 0xd0 0xe0 0xf0
* AP: 0x00 0x10 0x20 0x30 0x40 0x50 0x60 0x70 0x80 0x90 0xa0 0xb0 0xc0 0xd0 0xe0 0xf0
* AP/VLAN: 0x00 0x10 0x20 0x30 0x40 0x50 0x60 0x70 0x80 0x90 0xa0 0xb0 0xc0 0xd0 0xe0 0xf0
* mesh point: 0x00 0x10 0x20 0x30 0x40 0x50 0x60 0x70 0x80 0x90 0xa0 0xb0 0xc0 0xd0 0xe0 0xf0
* P2P-client: 0x00 0x10 0x20 0x30 0x40 0x50 0x60 0x70 0x80 0x90 0xa0 0xb0 0xc0 0xd0 0xe0 0xf0
* P2P-GO: 0x00 0x10 0x20 0x30 0x40 0x50 0x60 0x70 0x80 0x90 0xa0 0xb0 0xc0 0xd0 0xe0 0xf0
* P2P-device: 0x00 0x10 0x20 0x30 0x40 0x50 0x60 0x70 0x80 0x90 0xa0 0xb0 0xc0 0xd0 0xe0 0xf0
Supported RX frame types:
* IBSS: 0x40 0xb0 0xc0 0xd0
* managed: 0x40 0xd0
* AP: 0x00 0x20 0x40 0xa0 0xb0 0xc0 0xd0
* AP/VLAN: 0x00 0x20 0x40 0xa0 0xb0 0xc0 0xd0
* mesh point: 0xb0 0xc0 0xd0
* P2P-client: 0x40 0xd0
* P2P-GO: 0x00 0x20 0x40 0xa0 0xb0 0xc0 0xd0
* P2P-device: 0x40 0xd0
WoWLAN support:
* wake up on disconnect
* wake up on magic packet
* wake up on pattern match, up to 20 patterns of 16-128 bytes,
maximum packet offset 0 bytes
* can do GTK rekeying
* wake up on GTK rekey failure
* wake up on EAP identity request
* wake up on 4-way handshake
* wake up on rfkill release
* wake up on TCP connection
software interface modes (can always be added):
* AP/VLAN
* monitor
valid interface combinations:
* #{ managed } <= 1, #{ AP, P2P-client, P2P-GO } <= 1, #{ P2P-device } <= 1,
total <= 3, #channels <= 2
HT Capability overrides:
* MCS: ff ff ff ff ff ff ff ff ff ff
* maximum A-MSDU length
* supported channel width
* short GI for 40 MHz
* max A-MPDU length exponent
* min MPDU start spacing
Device supports TX status socket option.
Device supports HT-IBSS.
Device supports SAE with AUTHENTICATE command
Device supports low priority scan.
Device supports scan flush.
Device supports per-vif TX power setting
P2P GO supports CT window setting
P2P GO supports opportunistic powersave setting
Driver supports a userspace MPM
Device supports static SMPS
Device supports dynamic SMPSDisturbing Linux services
When using a standard Linux client distribution, there may be services, which are disruptive for wireless capturing. Examples are “avahi-daemon”, “NetworkManager”, “wpa_supplicant” or “dhclient”. If your capture stops at some point without a reason, try to temporarily disable those services.
Example: sudo service NetworkManager stop
Create monitoring interface
Now we can create a new monitoring network interface. As the name already states, that interface is in monitoring / promisuous mode. The second command removes the main WLAN interface.
sudo iw phy0 interface add mon0 type monitor
sudo iw dev wlp2s0 del
sudo ifconfig mon0 upSet capture parameters
As written in my previous post, the capture channel must be set.
Either set the freqency using:
sudo iw dev mon0 set freq <FREQ-IN-MHZ>or the channel number using:
sudo iw dev mon0 set channel <CHANNEL-NUMBER>If you add the parameter HT40+, you capture 40MHz wide channels:
sudo iw dev mon0 set channel <CHANNEL-NUMBER> HT40+Verify your configuration:
iw mon0 info
Example output:
Interface mon0
ifindex 4
wdev 0x3
addr 80:86:f2:6d:58:ad
type monitor
wiphy 0
channel 11 (2462 MHz), width: 20 MHz (no HT), center1: 2462 MHzCapture using tcpdump to capture file
If you like to use tcpdump for capturing, issue the following command:
sudo tcpdump -i mon0 -w capture.capAlternatively, you can capture using Wireshark
Radiotap header
One nice side effect is, that a radiotap header is added to the capture frame. This information is NOT inside a WLAN frame. It is added by the capturing device to each frame to get some RF information (RSSI, channel, data rate etc.)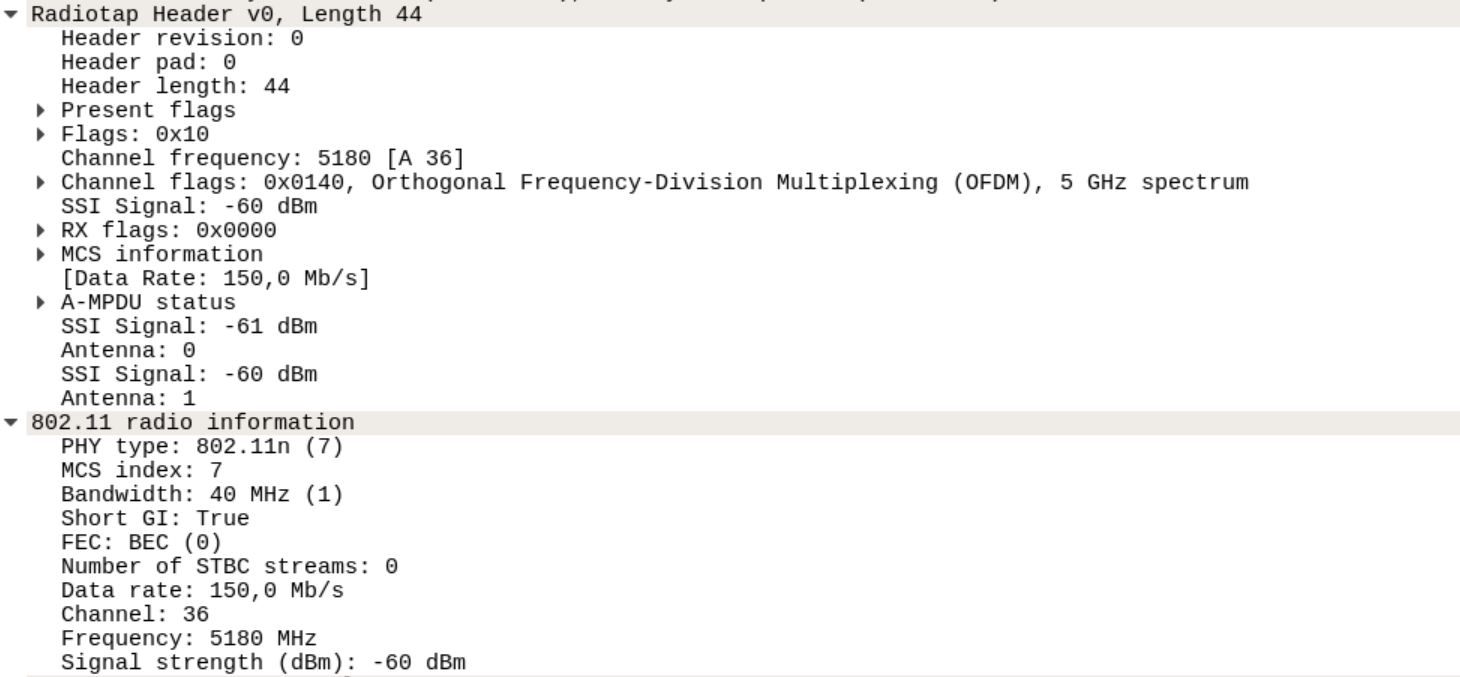
This is a WireShark screenshot of the radiotap header. In tcpdump the output looks like:
09:31:19.120447 54.0 Mb/s 5180 MHz 11a -59dB signal [bit 29] Request-To-Send TA:40:b8:37:b3:e2:0e (oui Unknown)
09:31:19.120457 54.0 Mb/s 5180 MHz 11a -48dB signal [bit 29] Clear-To-Send RA:40:b8:37:b3:e2:0e (oui Unknown)
09:31:19.120515 5180 MHz 11a -59dB signal 150.0 Mb/s MCS 7 40 MHz short GI BCC FEC RX-STBC0 [bit 20] CF +QoS Data IV:945 Pad 20 KeyID 0
09:31:19.120549 54.0 Mb/s 5180 MHz 11a -47dB signal [bit 29] BA RA:40:b8:37:b3:e2:0e (oui Unknown)
09:31:19.163533 54.0 Mb/s 5180 MHz 11a -59dB signal [bit 29] CF +QoS
09:31:19.163544 54.0 Mb/s 5180 MHz 11a -48dB signal [bit 29] Acknowledgment RA:40:b8:37:b3:e2:0e (oui Unknown)
09:31:19.297174 54.0 Mb/s 5180 MHz 11a -63dB signal [bit 29] CF +QoStcpdump capture filters
You’ll see very soon, that you are overwhelmed with frames. So it’s probably a good idea to appy a capture filter.
Here are some examples:
(usage sudo tcpdump -i mon0 -w capture.cap <FILTER>)
- Capture only beacon frames: subtype beacon
- Capture only probe requests or responses: subtype probereq or subtype proberesp
- Only from an to a wireless host: wlan ra <CLIENT-MAC> or wlan ta <CLIENT-MAC>
- Filter of packet types:
- Management frames: type mgt
- Control frames: type ctl
- Data frames: type data
Note: You won’t see any control frames (RTS,CTS etc.) when using the “wlan ra” or “ta” filters. I’ll explain those filters in detail in another post.


1 Comment
Cisco WLC: EDCA timers - NetGab - The daily networking madness · 05/12/2017 at 16:45
[…] Unfortunately the actual values cannot be determined in the WLC GUI or CLI. Furthermore, the names of the EDCA profiles don’t reflect whether the IEEE 802.11 parameters are used. The good thing is, that the values can be captured in beacon frames. If you don’t know how to capture wirless frames, please check these posts: WLAN traffic capture [1] and WLAN traffic capture [2] […]